Construction
Construction companies are fast becoming a favoured target among cybercriminals.
Construction firms are currently dealing with a huge array of new risks – both on and offsite. A threat can expose all of a company’s digital assets, including business plans and acquisition strategies; proprietary construction plans and designs; customer, contractor, and supplier lists and pricing; personally identifiable information (PII) of employees and contractors; protected health information of staff as well as facilities security information. Threats can also severely interrupt the manufacturing and building process, hit profit margins, and cause reputational damage.

Some Key Areas To Review
Key NIST/CyberSecure Canada control points:

Fusion Computing targeted remediation:
Risk Assessments
Risk must be gauged and prioritized based on factors such as probability of occurrence, impact on the organization, and prioritization.
Risk assessments should be conducted or reviewed regularly and at least once per year.
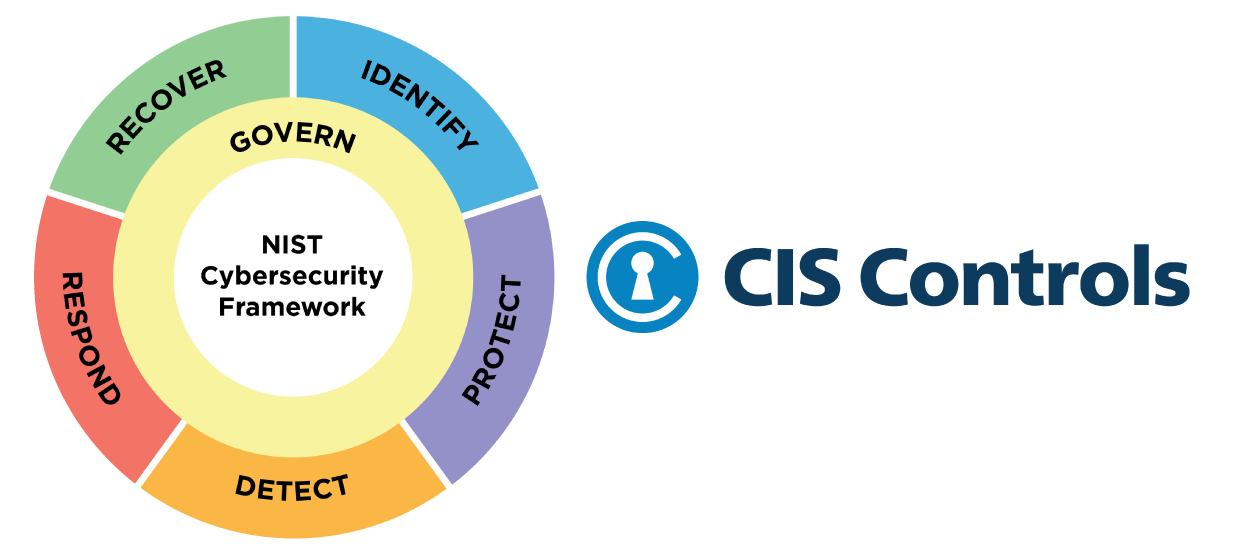
The CIS Critical Security Controls (CIS Controls) are a prescriptive, prioritized, and simplified set of best practices Fusion uses to strengthen your cybersecurity posture. This simplified cybersecurity approach is proven to help you defend against today’s top threats.
Testimonials
See why top employers and small business leaders say Fusion is the Best IT Company in Toronto
Latest Blogs
Learn about critical IT topics from our experts. We cover everything from new cloud based tools, to IT outsourcing and disaster recovery.



