Transport & Logistics
Although digital transformation and automation of the transport and logistics sector are proving to be a boon, they have also made the industry an easy and sought-after target for cybercrime.
As most or all levels of the supply chain are rapidly integrated with the cloud, significant cybersecurity risks have emerged. This sector is particularly vulnerable to cyber-related incidents with many stakeholders and third-party vendors in the logistics chain.

Some Key Areas To Review

In May 2021, the Colonial Ppolhe attack disrupted jet fuel and gasoline supplies to large areas of the southeastern region of the U.S. While the direct financial Impact was the payment of a $4.4 million ransom, the Indirect financial and socioeconomic Impacts to the associated supply chain were far greater. The crippling attack cost the company $40 million in charges on lost shipping opportunities and a further $20 million in investigation, recovery and remediation expenses.
Key NIST/CyberSecure Canada control points:

Fusion Computing targeted remediation:
Risk Assessments
Risk must be gauged based on factors such as probability of occurrence, impact on the organization, and risk prioritization.
Risk assessments should be conducted or reviewed regularly and at least once per year.
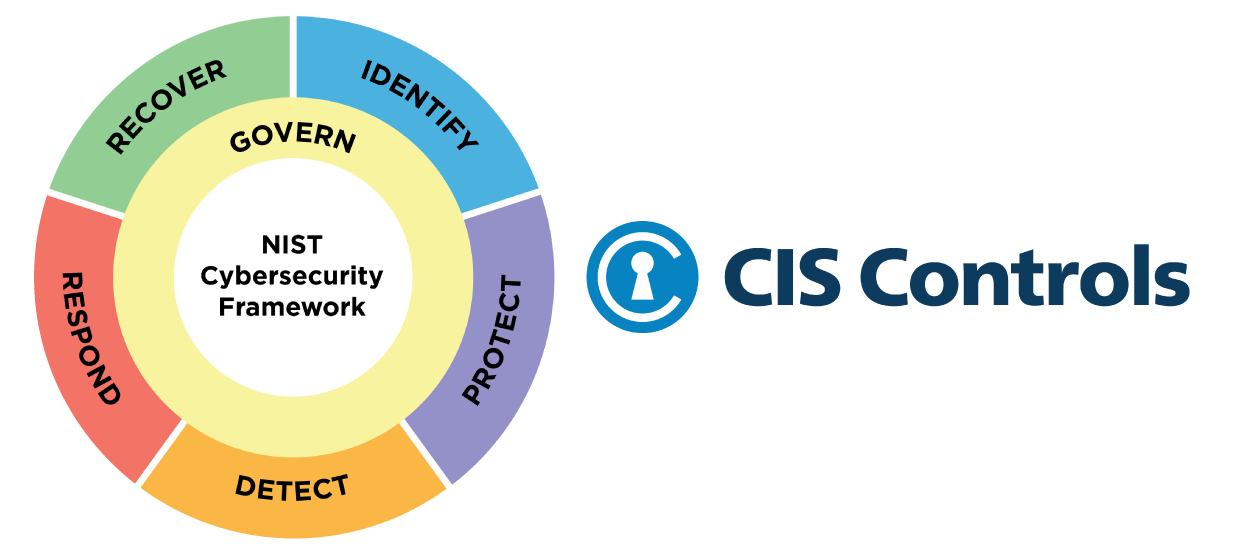
The CIS Critical Security Controls (CIS Controls) are a prescriptive, prioritized, and simplified set of best practices Fusion uses to strengthen your cybersecurity posture. This simplified cybersecurity approach is proven to help you defend against today’s top threats.
Testimonials
See why top employers and small business leaders say Fusion is the Best IT Company in Toronto
Latest Blogs
Learn about critical IT topics from our experts. We cover everything from new cloud based tools, to IT outsourcing and disaster recovery.



