While most companies offer Managed Service Provider (MSP) services, Fusion Computing offers the next level of service called Technology Success Partner (TSP) Services.
Technology Success Partners surpass MSPs by aligning technology with business goals. They leverage deeper vendor relationships, retain top engineers, and embrace cutting-edge solutions. TSPs prioritize technology leadership and offer simplified, cutting-edge IT solutions. They ensure clients always have the right technology for their business, driving growth and operational maturity.
Would you like to understand more about TSP vs. other service options – Read our Blog.
Are constant IT issues getting in the way of running your business?
Our TSP services include monitoring your IT systems 24/7/365 to fix issues before you notice them and upgrade your IT in the process.
Our Clients
Testimonials
See why top employers and small business leaders say Fusion is the Best IT Company in Toronto
As your Technology Success Partner, you will benefit from:
OUR NUMBERS
What Sets Our TSP Service Apart?
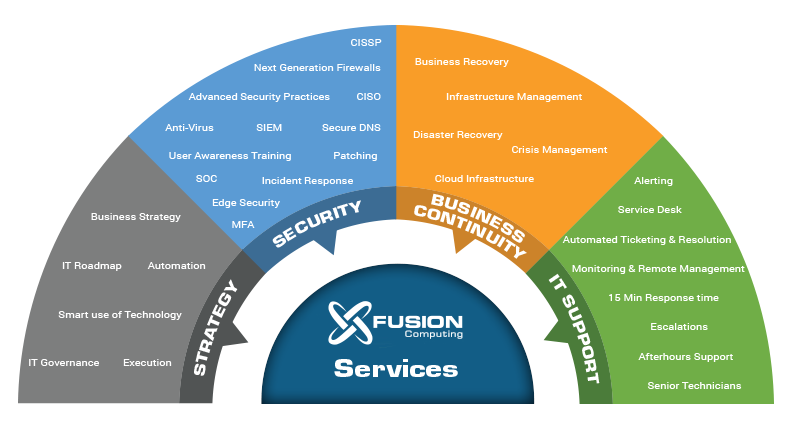
What You Get with Our TSP Services

Get IT Issues Fixed Whenever They Happen
IT issues slow down your entire company and force your team to jump into troubleshooting instead of working on critical projects.
You shouldn’t have to lose hours or even days of productivity every time something in your IT breaks down.
At Fusion Computing, our Technology Success Partner (TSP) services ensure rapid responses to your service desk tickets, with an average response time of just 6 minutes. Remarkably, 93% of issues are resolved in under 1 hour.
Your toughest problems will get fixed on the same day with our in-house tech support services team of hardware and software experts who are local to the Toronto area.
Solve Issues The Same Day
Get your IT, business continuity and cyber security issues resolved without needing to spend hours on the phone with tech support explaining problems and waiting for troubleshooting.
We’ll put a senior technician in charge of your IT as a lead project manager – so when things go down, you deal with one person who is completely familiar with your systems.
Once you call, your job is done. Your technician at Fusion Computing will handle everything with a team in-house, and you’ll never have to wait for a 3rd party to “schedule you in.”


Put An End To Recurring Issues
Most of the time, you’re stuck fixing issues that keep popping up because something in your network isn’t up to par.
We’ll audit your entire network, and proactively find and provide IT solutions that fix the root causes of recurring issues and downtime.
Most clients experience as much as a 58% reduction in IT issues within their first 90 days with Fusion Computing as their TSP.
Meanwhile, tracking systems flag upcoming problems in your network, and we resolve them before you notice anything.
Reduce Your Costs Over Time
Like most businesses, there are hundreds of manual processes across your company that quietly drain your budgets and create a lot of busywork.
Your IT manager works with business consultants at Fusion Computing to implement automations that eliminate manual processes across your company.
After a few months of IT outsourcing, you’ll save hundreds of hours across your admin, customer support, sales, and other departments with optimizations that you probably thought only enterprises could deploy.


Free Up Your Team
Get your in-house team focused on critical projects, not day-to-day system administration.
We’ll manage everything from applications and system design to network infrastructure administration and budgeting – so your in-house teams can start working on the business, not just keeping things running.
If you don’t have any in-house IT people, then we’ll handle everything right up to IT strategy and help you keep your team working on the business while the IT is taken care of.
Predictable in IT Expenditures
You’ll get fully costed short, and long term IT budgets with recommendations for hardware and software purchases that align to your business goals and objectives.
Your managed IT services and IT consulting from Fusion Computing come in one flat monthly fee that covers everything you need.
No more surprise expenses from IT. Just peace of mind and a clear picture of how costs will change in the future – it’s everything you’ve been asking for.









