Finance
Financial institutions are among the leading targets of cyber attacks.
Banks are where the money is; for cybercriminals, attacking banks offers multiple avenues for profit through extortion, theft, and fraud. At the same time, nation-states and hacktivists also target the financial sector for political and ideological leverage. Cyber-attacks in the financial sector have tripled over the past five years, and the average cost of containment has increased by 40%. Today, the assessment that a major cyberattack threatens financial stability is axiomatic- not a question of if, but when.

Some Key Areas To Review

More and more banking transactions are now conducted online, with 78% of Canadians primarily banking online or through mobile devices. After data breaches, It could be challenging to trust financial institutions. That’s a significant issue for banks. Data breaches caused by a shoddy cybersecurity solution may easily lead to their consumer base moving their business elsewhere.
Key NIST/CyberSecure Canada control points:

Fusion Computing targeted remediation:
Risk Assessments
Risk must be gauged based on factors such as probability of occurrence, impact on the organization, and prioritization.
Risk assessments should be conducted or reviewed regularly and at least once per year.
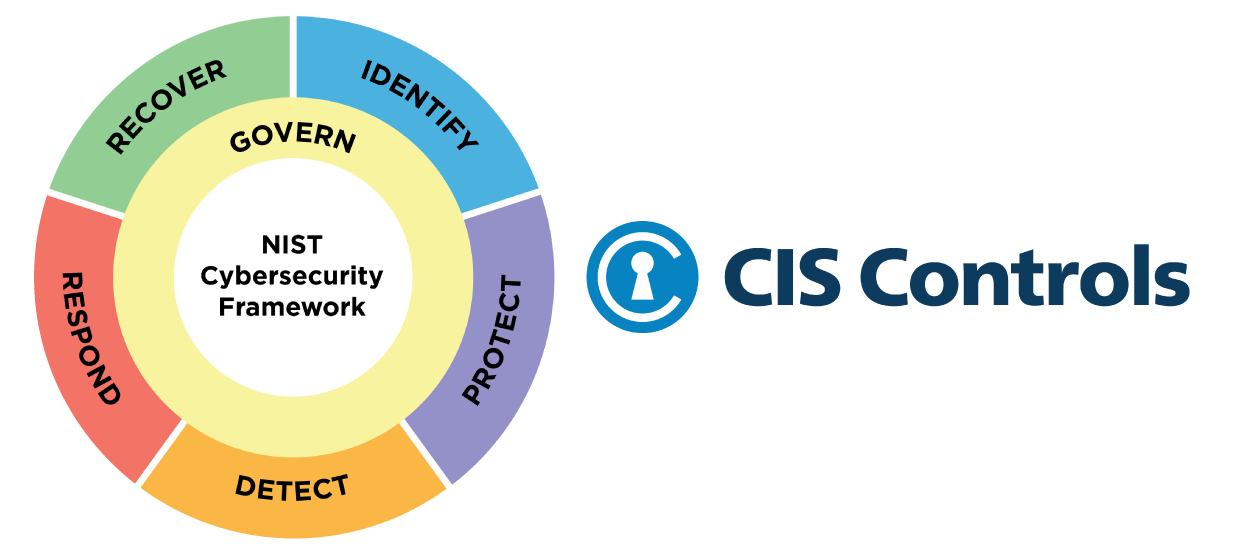
The CIS Critical Security Controls (CIS Controls) are a prescriptive, prioritized, and simplified set of best practices Fusion uses to strengthen your cybersecurity posture. This simplified cybersecurity approach is proven to help you defend against today’s top threats.
Testimonials
See why top employers and small business leaders say Fusion is the Best IT Company in Toronto
Latest Blogs
Learn about critical IT topics from our experts. We cover everything from new cloud based tools, to IT outsourcing and disaster recovery.



