Legal
Legal law firms are vulnerable targets for cyber attacks.
Law firms are often victims of cyberattacks because they have sensitive (and valuable) information about multiple companies or entities, usually housed in a single database. This makes firms “one-stop shops” for cybercriminals since they can obtain the desired data on various companies via a single source.

Some Key Areas To Review

Cyber security Insurance provides an additional level of security for firms that suffer from a data breach. While insurance does little to protect the stolen data, some policies do compensate for certain financial impacts of a breach, such as any fees associated with restoring the data, loss of income due to downtime, crisis management, or forensic Investigations.
Key NIST/CyberSecure Canada control points:

Fusion Computing targeted remediation:
Risk Assessments
Risk must be gauged based on factors such as probability of occurrence, impact on the organization, and prioritization.
Risk assessments should be conducted or reviewed regularly and at least once per year.
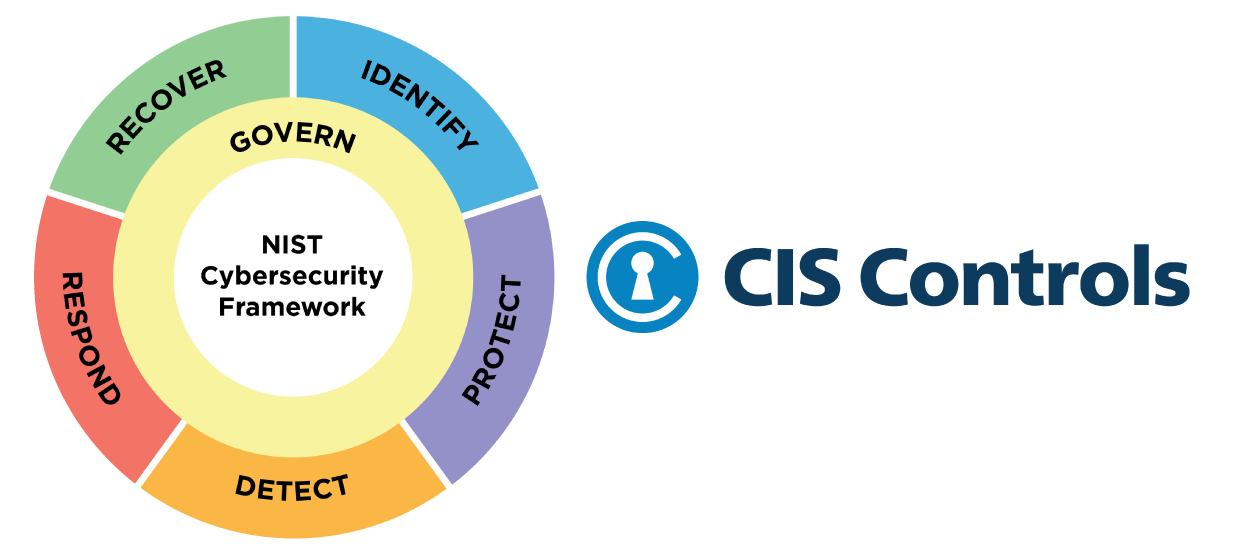
The CIS Critical Security Controls (CIS Controls) are a prescriptive, prioritized, and simplified set of best practices Fusion uses to strengthen your cybersecurity posture. This simplified cybersecurity approach is proven to help you defend against today’s top threats.
Testimonials
See why top employers and small business leaders say Fusion is the Best IT Company in Toronto
Latest Blogs
Learn about critical IT topics from our experts. We cover everything from new cloud based tools, to IT outsourcing and disaster recovery.



