IT assessments cost time and money. They can be resource-intensive, for the duration of the audit. However, that old saying, “an ounce of prevention is worth a pound of cure” holds true in IT. Audits must be done to ensure the well-being and future viability of the company.
First, let’s define what an IT assessment (sometimes referred to as a technology assessment) is.
An IT assessment is a documented audit of information systems that are associated with the business, including its hardware and software, leased or owned equipment, and cloud services (on or off-premises).
Also included in the audit are the daily processes of the company and how they relate to products and services, so they can be itemized and summarized in the final audit report.
If the equipment is used by the company in the course of doing business, it is included in the audit. Equipment not used is also included, provided the company owns or is paying money to possess it. This ensures a complete picture of company assets, including redundant items that don’t contribute (or are detrimental) to the bottom line.
Why Should You Conduct an IT Assessment?
Any problem with your information technology system can impact your business, costing you time and money while you try to get systems up and running. One of the best ways to prevent issues is having visibility into your IT stems, which allows you to effectively plan risk management. This can also aid in formulating a disaster recovery plan.
A complete IT assessment provides insight into what the organization is doing right, and what can be improved. It can reveal:
- Inadequate security systems
- Vulnerable access points
- Outdated software
- Obsolete or redundant hardware and processes
- Lax staff training
- Identifying who has access to the network
- And more
| Not Sure What Your IT Audit Should Include?
Find out how you can evaluate your IT environment, operations and policies. |
Assessments can provide insight not only on what technology systems might be needed to achieve business goals but also on what problems interfere with daily operations. Inefficiencies, error rates, and bottlenecks might be known only in a general sense, with an elusive solution. An assessment can reveal details that help pinpoint the underlying cause of the issue.
In other words, an assessment of systems and connected processes will not only help you identify the problem but also help you find the solution. And going forward, the use of established routines and industry best practices will help keep the company secure, efficient, and agile, while streamlining the decision-making process.
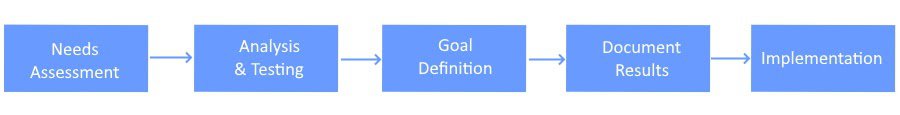
Technology Assessment Checklist
The best assessments take a holistic approach to the entire organization. That is, looking at each individual piece to see the larger picture. This technology checklist should include not only an examination of the role technology and people play within your organization, but also your relationship with the customers you serve.
1) Needs Assessment & Discovery
Understand the current state of your business, and its technology environment. Include input from a variety of stakeholders within the organization, including managers, IT specialists, equipment users, maintenance staff, sales staff, and others as deemed necessary.
Know what assets (people, operating systems, software, and hardware) you have, and why they were chosen.
Who are your customers, and what are their needs? Are those needs being met, or are some customers looking elsewhere? Ultimately, you exist to serve your customers. Your whole business has been built with that result in mind, and is the ultimate driver for the assessment process.
2) Analysis & Testing
Determine where things stand internally when it comes to:
- Regulatory compliance
- Software update status
- Systems that may be causing inefficiencies
- Protecting critical data from attack or accidental loss
- Reducing risks associated with technology change
- Business continuity and disaster recovery plans
- Onboarding and refresher training
Document and assess the above points, to find out if they are presently given adequate attention, and are being used as designed. Understand where they may be lacking.
| Learn More: |
3) Goal Definition
Understand the future goals of the company and any short-term issues that need addressing. Will the existing network infrastructure and processes satisfy those goals, or will changes be needed?
Ensure there is alignment between users and developers, customers and production. Do the present technologies satisfy those groups and their future needs?
Come up with a reasonable budget and timeframe to reach those goals.
4) Document Results
Create a complete report of the items discussed above, including:
- Executive summary
- Explanations of issues
- Details of solution implementation
- Deployment plan
- Timelines and project management ownership
There’s no point in producing the audit if the results won’t be shared as widely as is feasible within the organization. Documentation should be available to all relevant stakeholders. At the very least, the executive summary of the audit should be shared with team members who have input in the day-to-day business of the company.
Present the report to decision-makers, and discuss implementation plans. One-on-one meetings are most effective, followed by a collective meeting. Defend the report, but also accept feedback from SMEs.
5) Implementation
Based on the findings of the assessment, and consultation with stakeholders and SMEs, an implementation schedule is created, taking into account the allotted budget and timeframe. Assign persons to drive the process to completion.
Completed Your IT Assessment Checklist? It’s Take to Take Action
Technology can be a great boon to productivity, but only if the right systems are used correctly. Incorrect implementation, lack of adequate training, and obsolete systems can not only introduce errors and bottlenecks, but also put your organization at risk.
An information technology assessment checklist, when completed properly, can provide valuable insight as to the inner workings of the company, its efficiencies, and its problems. Methodically working through the assessment will help the organization in its personnel and purchase decisions, with a higher degree of confidence that any future changes will be the right ones.
Discuss your findings with us today. Our team helps businesses like yours exploit core strengths and address gaps.